一般的篩選 (Filter) 功能僅能針對時間範圍或 Event ID 進行搜尋,無法精確過濾更細項的資訊(如 Logon Type)。然而,透過 XML 搜尋,使用者可以更靈活地排除或包含特定類型的事件,並將查詢語法保存下來。這樣的查詢可在外部程式(如 PowerShell)中自動化運行,並重複使用,提升操作效率。
延續上一章XML格式,分成System及EventData兩大類,於撰寫搜尋語法時需分別用[]框起來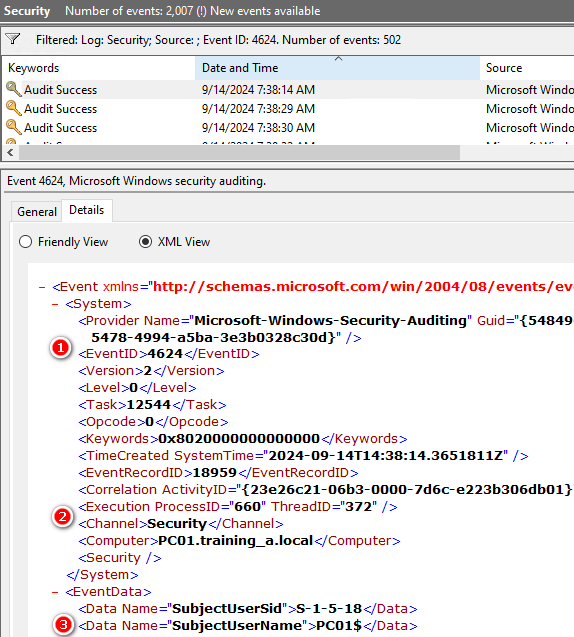
可以先設定一些過濾,切換到XML頁面時會自動產出搜尋語法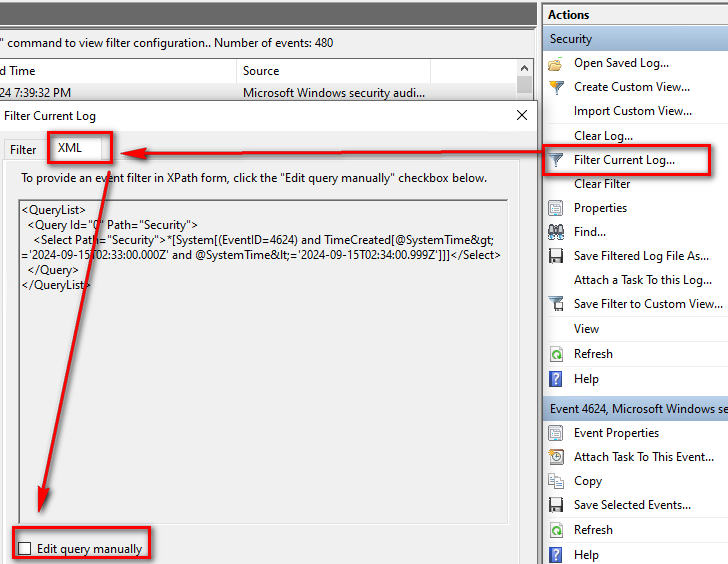
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">
*[System[
(EventID=4624 or EventID=4625)]
]
</Select>
</Query>
</QueryList>
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">
*[System[
(EventID=4624)
and
TimeCreated[timediff(@SystemTime) <= 86400000]]
]
</Select>
</Query>
</QueryList>
另一種時間區間寫法
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">
*[System[
(EventID=4624)
and
TimeCreated[@SystemTime>='2024-09-14T00:00:00.000Z' and @SystemTime<='2024-09-15T00:00:00.000Z']]
]
</Select>
</Query>
</QueryList>
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">
*[System[
(EventID=4624)
and
TimeCreated[timediff(@SystemTime) <= 86400000]
]
and
EventData[Data[@Name='LogonType'] and (Data='3')]
]
</Select>
</Query>
</QueryList>
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">
*[System[
(EventID=4624)
and
TimeCreated[timediff(@SystemTime) <= 86400000]
]
and
EventData[Data[@Name='LogonType'] and (Data='3')]
and
EventData[Data[@Name='AuthenticationPackageName'] and (Data='NTLM')]
]
</Select>
</Query>
</QueryList>
Windows XML Event Log (EVTX) format
https://github.com/libyal/libevtx/blob/main/documentation/Windows%20XML%20Event%20Log%20(EVTX).asciidoc
Event Queries and Event XML
https://learn.microsoft.com/en-us/previous-versions/bb399427(v=vs.90)?redirectedfrom=MSDN
Consuming Events (Windows Event Log)
https://learn.microsoft.com/en-us/windows/win32/wes/consuming-events?redirectedfrom=MSDN#limitations
Microsoft Security auditing
https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-10/security/threat-protection/auditing/event-4624
